Articles
-
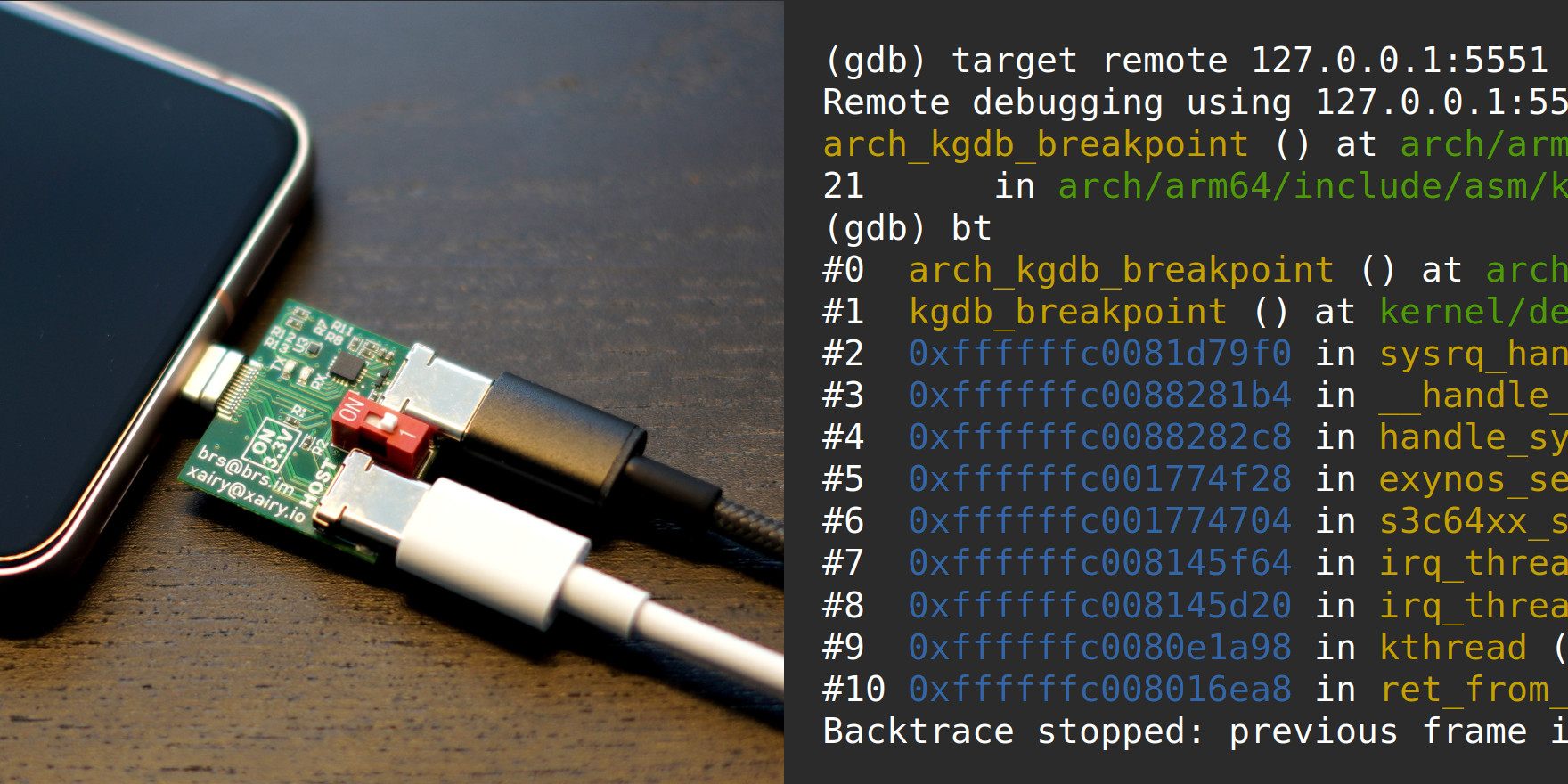
📲 Debugging the Pixel 8 kernel via KGDB
This article shows how to use GDB over a serial connection for debugging the kernel on a Pixel 8.
The instructions cover building and flashing a custom Pixel 8 kernel to enable KGDB, breaking into KGDB either via ADB by relying on
/proc/sysrq-triggeror purely over a serial connection by sending the SysRq-G sequence, and attaching GDB to the Pixel 8 kernel.The instructions should be adaptable to other Pixels as well.
-
🤫 Unlocking secret ThinkPad functionality for emulating USB devices
This is the story of how I figured out a way to turn my ThinkPad X1 Carbon 6th Gen laptop into a programmable USB device by enabling the xDCI controller.
As a result, the laptop can now be used to emulate arbitrary USB devices such as keyboards or storage drives. Or to fuzz USB hosts with the help of Raw Gadget and syzkaller. Or to even run Facedancer with the help of the Raw Gadget–based backend. And do all this without any external hardware.
The journey of enabling xDCI included fiddling with Linux kernel drivers, xHCI, DWC3, ACPI, BIOS/UEFI, Boot Guard, TPM, NVRAM, PCH, PMC, PSF, IOSF, and P2SB, and making a custom USB cable 😱
-
🔍 Looking for Remote Code Execution bugs in the Linux kernel
How would an attacker remotely take over a personal Linux or Android device? Send a malicious link and get code execution through the browser? Or target a messenger or an email client? Well, how about sending a series of network packets and owning the kernel directly 😋
This article covers my experience with fuzzing the Linux kernel externally over the network. I’ll explain how I extended a kernel fuzzer called syzkaller for this purpose and show off the found bugs. The article also includes an introduction to syzkaller and its advanced feature — pseudo-syscalls.
Sadly, to find that one bug to take over the Internet — I failed. But I did manage to find a one-shot RCE in a non-public kernel flavor.
-
🧾 Making offline Cardano transactions
While there are tools to make offline transactions on Ethereum, I’ve failed to find any comprehensive solution for Cardano. This post contains the instructions on creating an offline Cardano wallet and signing Cardano transactions offline with the help of command-line tools.
-
🐧 Ruffling the penguin! How to fuzz the Linux kernel

An overview article about approaches to Linux kernel fuzzing. Written together with the HackMag Editorial Board based on the Fuzzing the Linux kernel talk I gave at PHDays 2021.
This article is also available in Russian.
-
🌈 Highlighting syzkaller descriptions syntax with Rouge
Want to have fancy syntax highlighting for syzkaller snippets? I implemented it for syzlang — the language for describing syscall interfaces. The highlighting is based on Rouge — the default syntax highlighter on GitHub Pages. syzkaller programs can be highlighted as well.
-
🧰 Describing new subsystems for syzkaller

A collection of tips on writing new syscall descriptions for syzkaller.
-
⏲ CVE-2017-18344: Exploiting an arbitrary-read vulnerability in the Linux kernel timer subsystem
A mini-article about CVE-2017-18344 — an arbitrary-read vulnerability I found in the Linux kernel timer subsystem. Contains a brief description of the
/etc/shadowleak exploit I wrote for this bug. Originally posted as an announcement on the OSS-Security mailing list. -
👽 CVE-2017-1000112: Exploiting an out-of-bounds bug in the Linux kernel UFO packets
A mini-article about CVE-2017-1000112 — a memory corruption vulnerability I found in the UDP Fragmentation Offload feature of the Linux kernel IP sockets. Contains a brief description of the Local Privilege Escalation exploit I wrote for this bug. Originally posted as an announcement on the OSS-Security mailing list.
-
🖥 Tips on improving security of Ubuntu Desktop
A few simple tips on how to improve the security of an Ubuntu Desktop (or Linux Mint) installation.
-
🪲 Reporting Linux kernel bugs

A step-by-step guide on reporting Linux kernel bugs and doing a coordinated disclosure for security vulnerabilities.
-
🎒 CVE-2017-7308: Exploiting the Linux kernel via packet sockets

An article about how I found and exploited an out-of-bounds write vulnerability (CVE-2017-7308) in the Linux kernel packet sockets.
-
🌲 CVE-2017-6074: Exploiting a double-free in the Linux kernel DCCP sockets
A mini-article about CVE-2017-6074 — a double-free vulnerability I found in the Linux kernel DCCP sockets. Contains a brief description of the LPE exploit I wrote for this bug. Originally posted as an announcement on the OSS-Security mailing list.
-
 🏎 Автоматический поиск состояний гонок в ядре ОС Linux
🏎 Автоматический поиск состояний гонок в ядре ОС Linux

Моя магистерская работа в МФТИ. Основана на KTSAN — динамическом детекторе состояний гонок для ядра Linux.
-
🐝 CVE-2016-2384: Exploiting a double-free in the Linux kernel USB MIDI driver
While playing around with the vUSBf kernel fuzzer, I found a vulnerability (CVE-2016-2384) in the Linux kernel USB MIDI driver. I reproduced the bug with a Facedancer21 board and wrote an exploit to gain code execution within the kernel. My exploit requires user space cooperation, but the bug is exploitable externally provided one finds the right primitives.
-
 🐞 Автоматический поиск ошибок работы с динамической памятью в ядре ОС Linux
🐞 Автоматический поиск ошибок работы с динамической памятью в ядре ОС Linux

Моя бакалаврская работа в МФТИ. Основана на KASAN — динамическом детекторе повреждений памяти для ядра Linux.