A security engineer focusing on fuzzers, exploits, and mitigations for Linux and Android kernels.
-
🧰 Fuzzing the Linux Kernel [4 days]

This training guides security researchers and software engineers through the field of Linux kernel fuzzing. In a series of lectures and practical labs, the training explores using fuzzing for finding kernel memory corruption bugs and analyzing their security impact.
The training starts with an introduction to Linux kernel fuzzing. This part covers making kernel-specific fuzzing harnesses for finding bugs, evaluating the harness effectiveness, and using KASAN to analyze the root cause and security impact of discovered vulnerabilities.
The second part of the training focuses on syzkaller — the most widely-used Linux kernel fuzzer. This part covers setting up and running syzkaller in its default configuration and also customizing syzkaller for targeted fuzzing of specific kernel subsystems.
-
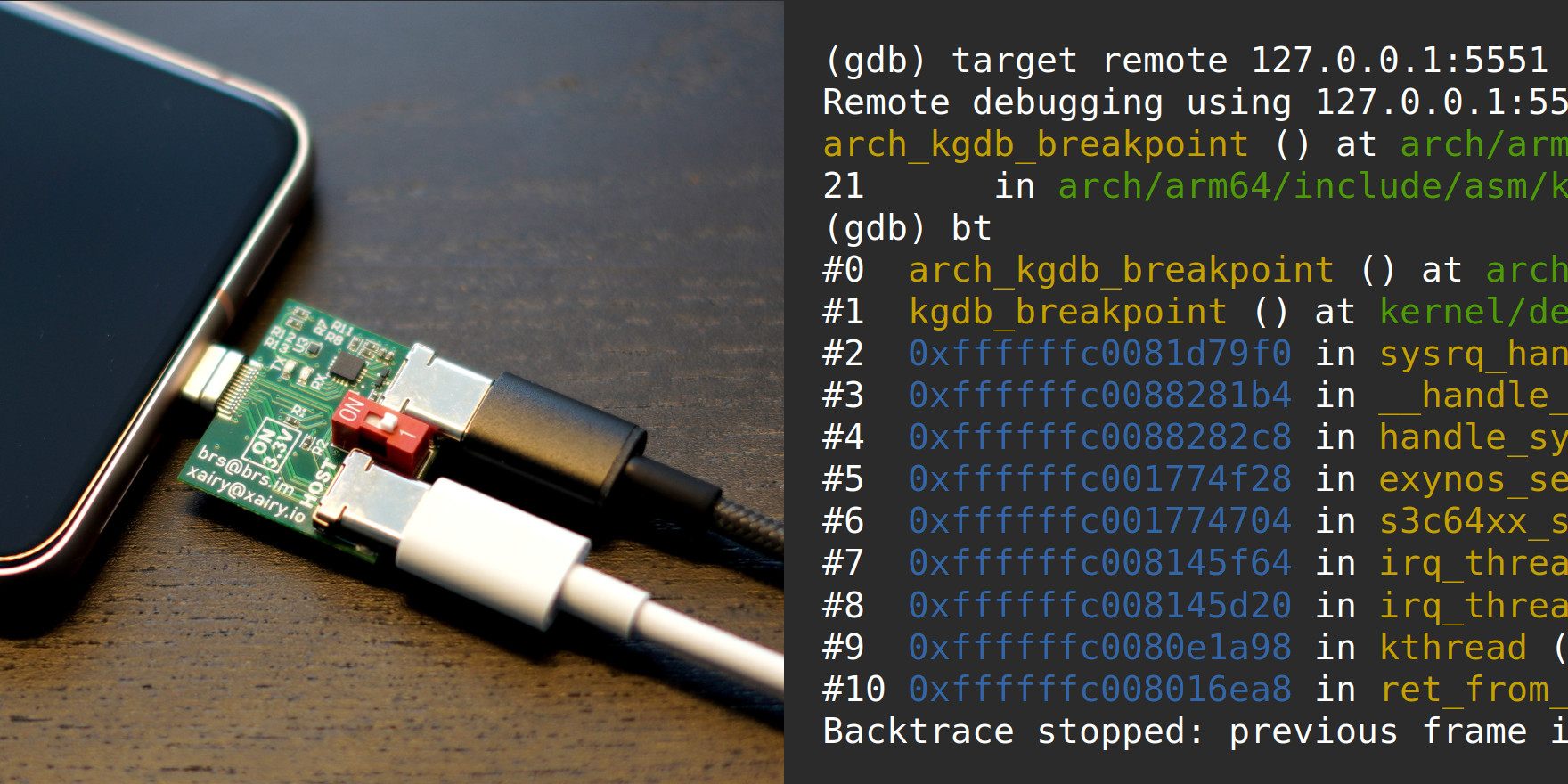
📲 Debugging the Pixel 8 kernel via KGDB
This article shows how to use GDB over a serial connection for debugging the kernel on a Pixel 8.
The instructions cover building and flashing a custom Pixel 8 kernel to enable KGDB, breaking into KGDB either via ADB by relying on
/proc/sysrq-triggeror purely over a serial connection by sending the SysRq-G sequence, and attaching GDB to the Pixel 8 kernel.The instructions should be adaptable to other Pixels as well.
-
🧱 SLUB Internals for Exploit Developers

A talk that covers the SLUB allocator internals and explains how common Slab shaping approaches work for exploiting Slab memory corruption bugs.
-
🥥 Linux Kernel Security channel

A Telegram channel about Linux kernel security. Me and Alexander Popov regularly post links to materials about exploits, fuzzers, mitigations, and other security-related things there.
The posts are also mirrored on X, Bluesky, Mastodon, and Reddit.