Trainings archive
-
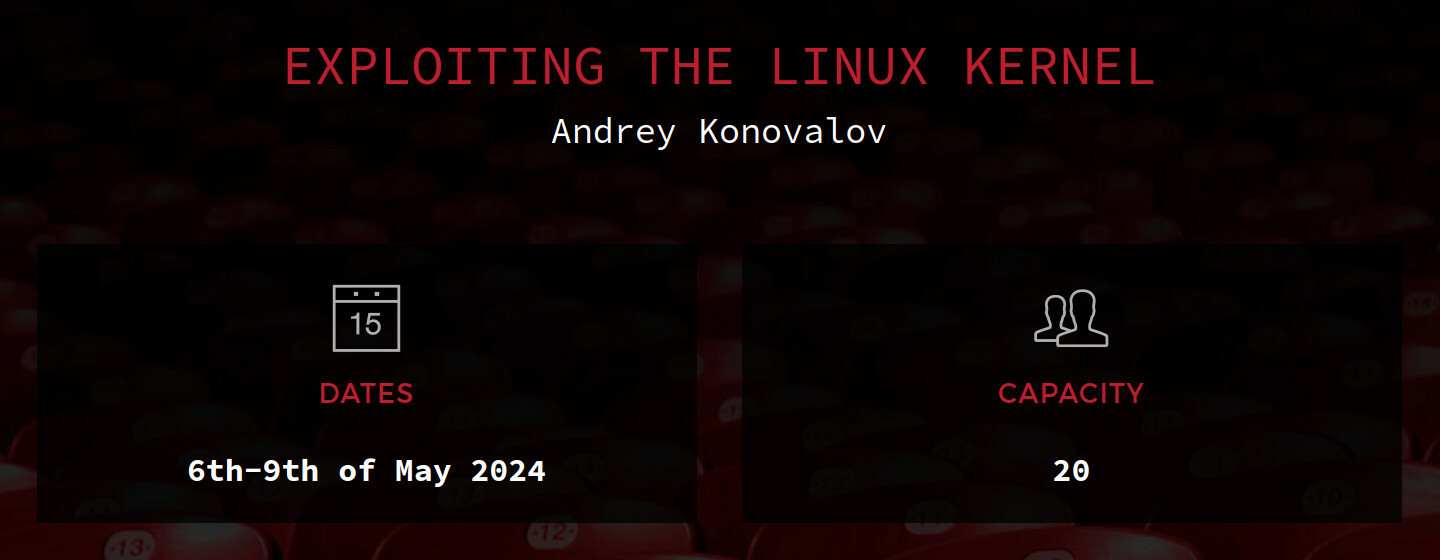
🗡 Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
🪓 Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
🧰 Fuzzing the Linux Kernel [2 days]

This training guides researchers through the field of Linux kernel fuzzing. In a series of practical labs, the training explores using syzkaller and KASAN for finding kernel memory corruption bugs and analyzing their security impact.
The training starts with an introduction to Linux kernel fuzzing. This part covers making kernel-specific fuzzing harnesses for finding bugs, evaluating the harness effectiveness, and using KASAN to analyze the security impact of discovered vulnerabilities.
The second part of the training focuses on syzkaller — the most widely used production-grade Linux kernel fuzzer. This part covers setting up and running syzkaller in its default configuration and also customizing syzkaller for targeted fuzzing of specific kernel subsystems.
-
⚔ Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
🗡 Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
⚔ Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
⚔ Exploiting the Linux Kernel [4 days]

A 4-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
⚔ Exploiting the Linux Kernel [3 days]

A 3-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
🗡 Exploiting the Linux Kernel [3 days]

A 3-day Linux kernel exploitation frenzy!
This training guides researchers through the field of Linux kernel exploitation. In a series of practical labs, the training explores the process of exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
The training starts with the beginner topics but proceeds into advanced areas as well. The beginner chapters include learning the techniques to escalate privileges and bypass foundational mitigations in x86-64 kernels. The advanced chapters are dedicated to slab (heap) exploitation, including an in-depth analysis of the kernel allocators’ internals.
-
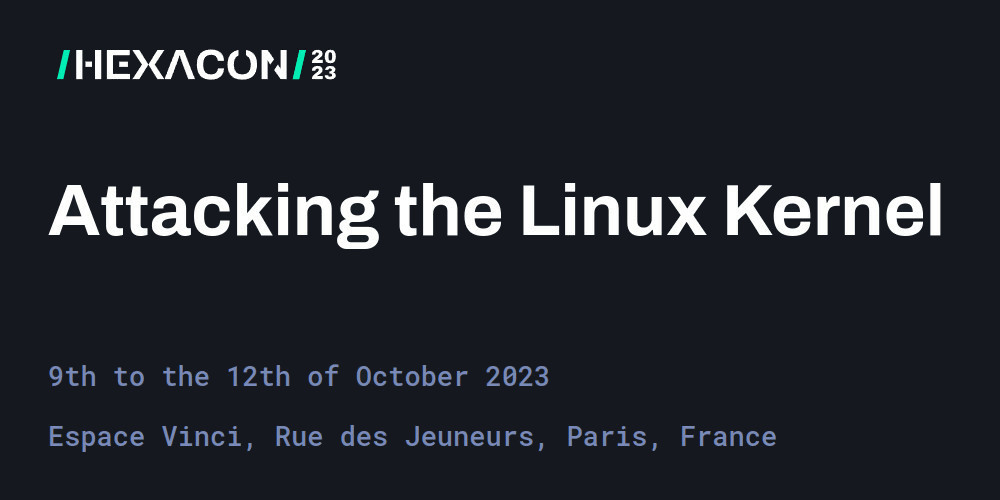
🪓 Attacking the Linux Kernel [4 days]

A 4-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
The training starts with the beginner topics but proceeds into a few advanced areas as well.
-
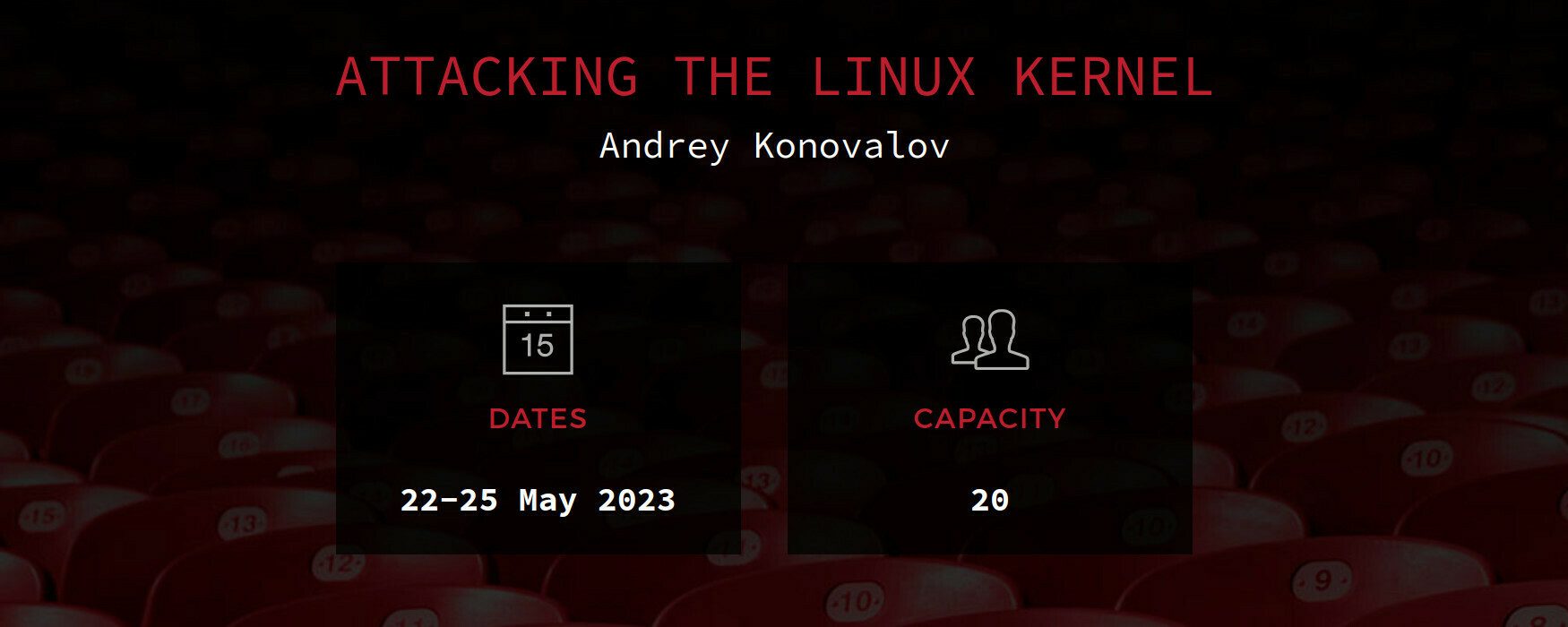
⚔ Attacking the Linux Kernel [3 days]

A 3-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
-
🗡 Attacking the Linux Kernel [4 days]

A 4-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
The training starts with the beginner topics but proceeds into a few advanced areas as well.
-
🪓 Attacking the Linux Kernel [4 days]

A 4-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in a modern Linux distribution on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
The training starts with the beginner topics but proceeds into a few advanced areas as well.
-
🗡 Attacking the Linux Kernel [2 days]

A two-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in modern Linux distributions on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
Targeted at beginners.
-
⚔ Attacking the Linux Kernel [2 days]

A two-day training that guides researchers through the field of Linux kernel security. In a series of exercise-driven labs, the training explores the process of finding, assessing, and exploiting kernel bugs in modern Linux distributions on the x86-64 architecture.
Besides providing a foundation for writing Linux kernel exploits, the training covers the no-less important areas of finding kernel bugs and evaluating their security impact. This includes chapters on using and extending dynamic bug-finding tools, writing custom fuzzers, and analyzing crashes.
Targeted at beginners.